How BOBcloud protects your cloud storage
Ransomware and other cybercrime attacks are the easiest way for criminals to extract money from you while maintaining anonymity.
This happens thousands of times yearly, and that number is increasing. Most attacks go unreported because of embarrassment or fear of customers losing faith in a business.
Since GDPR became law in the EU in May 2018, there have been reports of criminals blackmailing companies after downloading their customers’ data. This is because the fines for a personal data breach can run into millions, and a ransom payment might be considered an easier way out.
Many of your customers’ data might exist solely online, with one system admin accessing all systems with the same login credentials.
What if those credentials are shared between staff and the system administrator leaves your company? Will they still have backdoor access?
Organisations with a high admin staff turnover and highly privileged login accounts are the most vulnerable. Larger organisations also have the money to pay a ransom, so they are on the criminals’ ‘hit list’.
How a Cloud Storage Backup can help you recover from Ransomware


Send us BITCOINS
This is a typical scenario:
Someone with an available login to a customer’s server passes these details on to the criminal. They connect to the server and encrypt all files and data. Other attacks can come via malware downloaded by an unsuspecting user; however, those won’t typically grant unauthorised access to a server’s console.
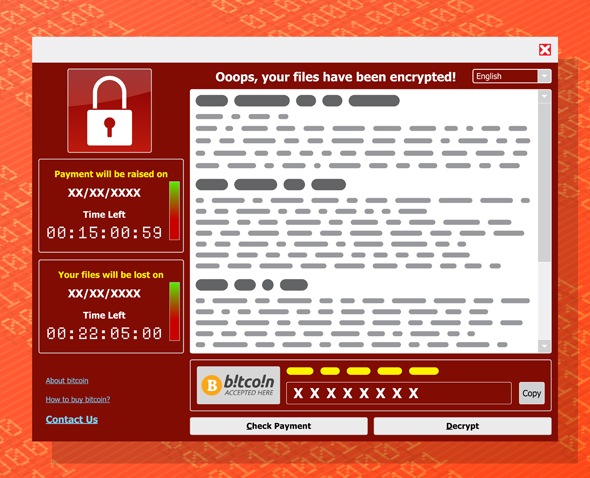

The backups are deleted as a final way to make sure a ransom is paid. Why? Because cybercriminals are intelligent and know the name and type of every backup, sync and replication product on the market.
They will download an application to the server and know within a few minutes about every backup, sync and replication product installed on your server. A few minutes later, they will all be purged, thus preventing a restore.
How can BOBcloud help?
It takes a few seconds to harden your BOBcloud backup sets and ensure all backed-up data is safe from cybercriminals.
Configure our software to log off whenever you use it on your customer’s server. Ideally, the software must be in a state requiring a login before being accessed. Under normal circumstances, a backup won’t need to be modified after the initial backup has finished, so it is unnecessary to give it an auto-login.
If the login becomes compromised, it can be easily changed.
